Search
Ad Hoc Searching: Global Pages
Events and Flows
There are two main databases that messages (logs) are stored in:
- Event Database: Contains the incoming message and how it got there (its metadata)
- Flow Database: Contains merged messages that shares a common tuple along with enhanced data
Both databases are useful and serve different purposes. These two databases can be searched via Network Flows and Event Search under Data Lake Section, respectively.
Message Flow
(This page is currently under "Legacy pages". Update it later.)
Login to the Fluency Cloud portal: https://(companyname).cloud.fluencysecurity.com.
Open the Main Menu from the upper left-hand corner and choose the Sources Devices option under the Data Ingress section.
Choose the "Diagram" tab, and it shows an active sankey diagram of information flowing through the system.
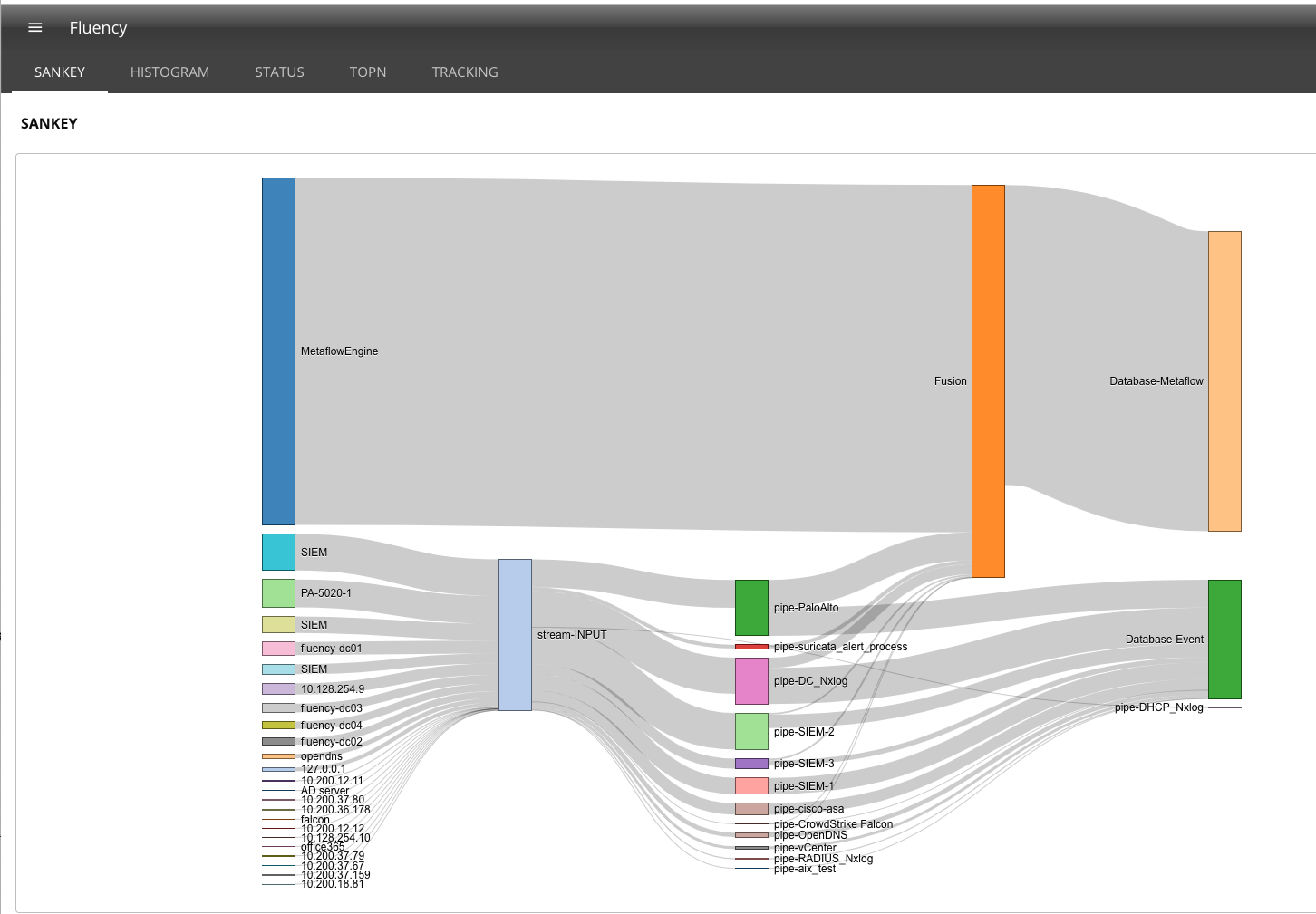
On the left side of the diagram is information entering the system.
Metaflow Engine data is the Fluency protocol analyzer adding flow data to fill in the gaps that are missed by the security tools. The boxes below that are data sources provide messages. The information is forwarded to the stream INPUT.
The message collector (stream INPUT) examines the message and sends it to the correct parser.
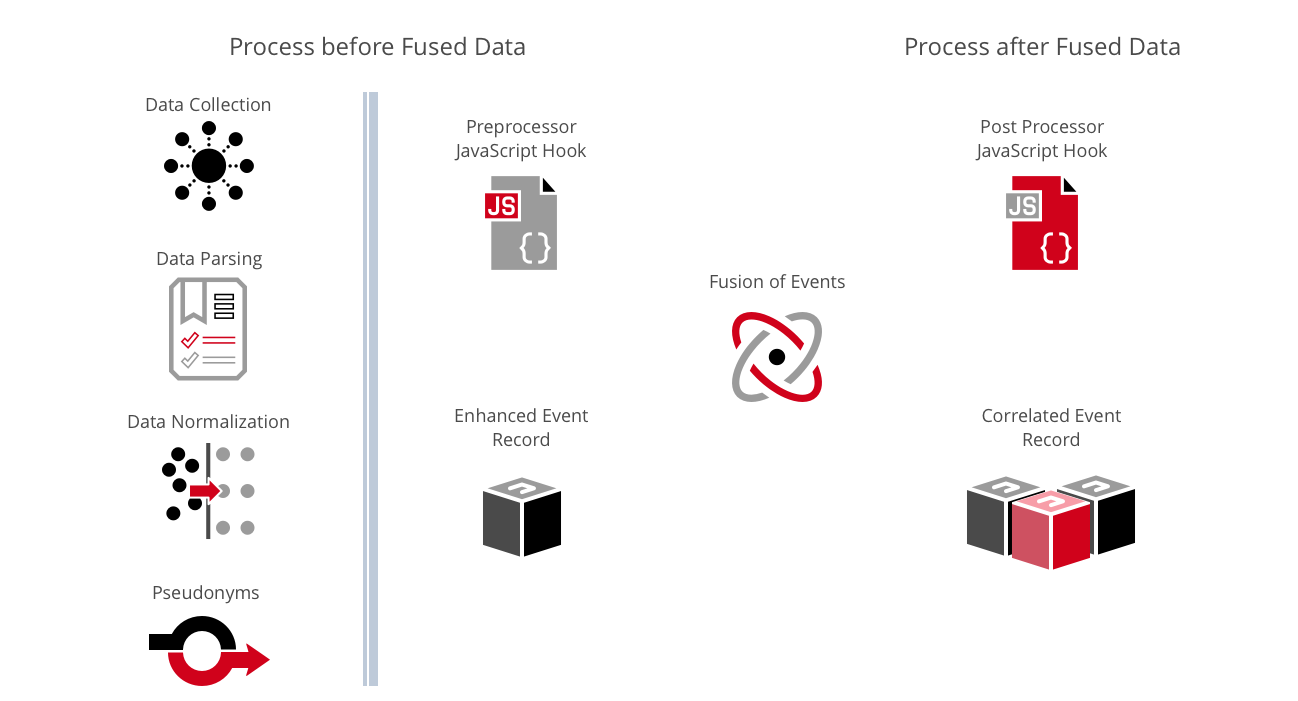
The parsers normalize the data into key-value fields producing a JSON document and define fields that are sensitive and have the value replaced with a Pseudonym.
The record and how the data is collected is placed in the Event Database and sent to the Fusion engine. The fusion engine enhances the record with table and third party lookups and merges the record with other records that share the same network tuple.
Before the record is stored, the RiskScore processor provides a confidence score and saved that data in the Flow Database.
Page last updated: 2023 Aug 10